Website hacking is a terrifying problem that can be disastrous for online businesses and website owners. A single hacking attempt can destroy thousands of dollars’ worth of investment, countless hours of work, carefully designed content, and more—in just a moment. For those of us who conduct business or work online, it’s crucial to stay vigilant about potential hacking threats.
A few weeks ago, I faced an unwanted hacking attempt on my website and email. In this article, I’ll share what happened, the steps I took to counter the issue, and how you can keep your website safe from such vulnerabilities. Let’s dive in vulnerable websites Category
Table of Contents
ToggleWhat Happened to My Website and Email?
One day, I logged into my hosting account and saw that my email account had been suspended. When I investigated further, I discovered it was due to abuse activity. My hosting provider flagged this issue, and they even sent me numerous emails detailing the reasons for the suspension—nearly 70 to 80 emails in total.
Since I didn’t use my company email regularly, all of these emails had gone unnoticed as I primarily relied on my personal email account. It wasn’t until I tried logging in to activate a link for signing up on a website using my company email that I realized something was wrong.
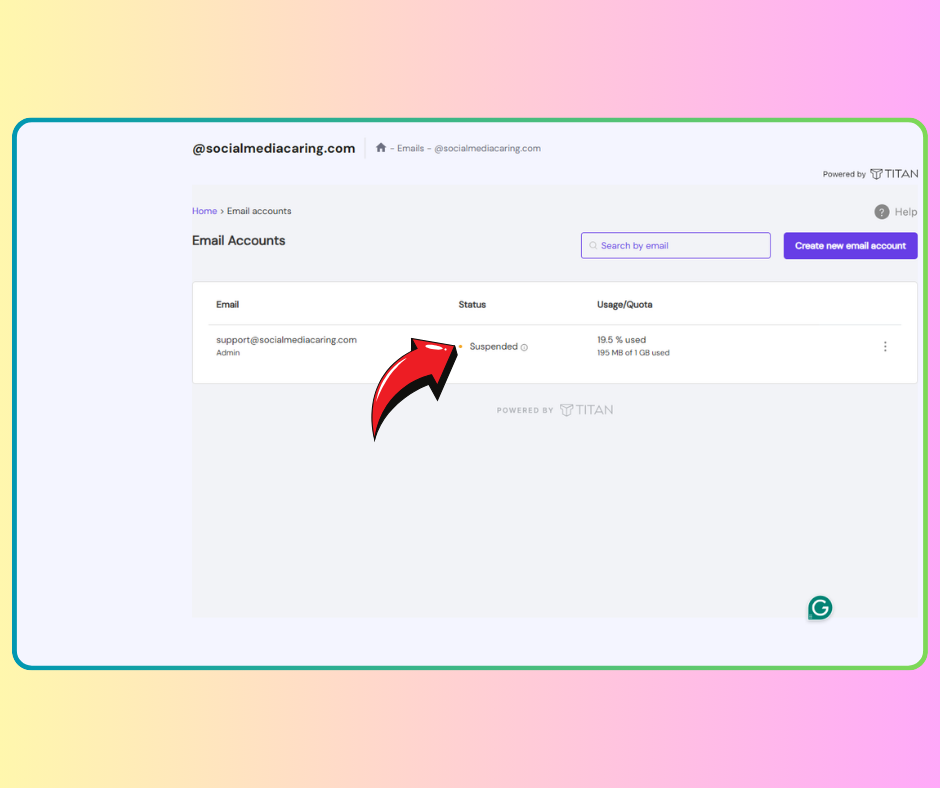
When I logged into my hosting account to check the email, I saw the dreaded message: “Email Account Suspended.” Below is a screenshot of the message I received.
At first, I thought the suspension was because I had exceeded my email’s daily limit. Just a few days earlier, I had sent out bulk emails while requesting guest posts for my website. I assumed that I had simply gone over the limit.
Since Titan Email was my service provider, I immediately sent them an email apologizing for what I thought was an unintentional mistake. I requested them to reactivate my email account, explaining that it wouldn’t happen again.
A Shocking Revelation vulnerable websites
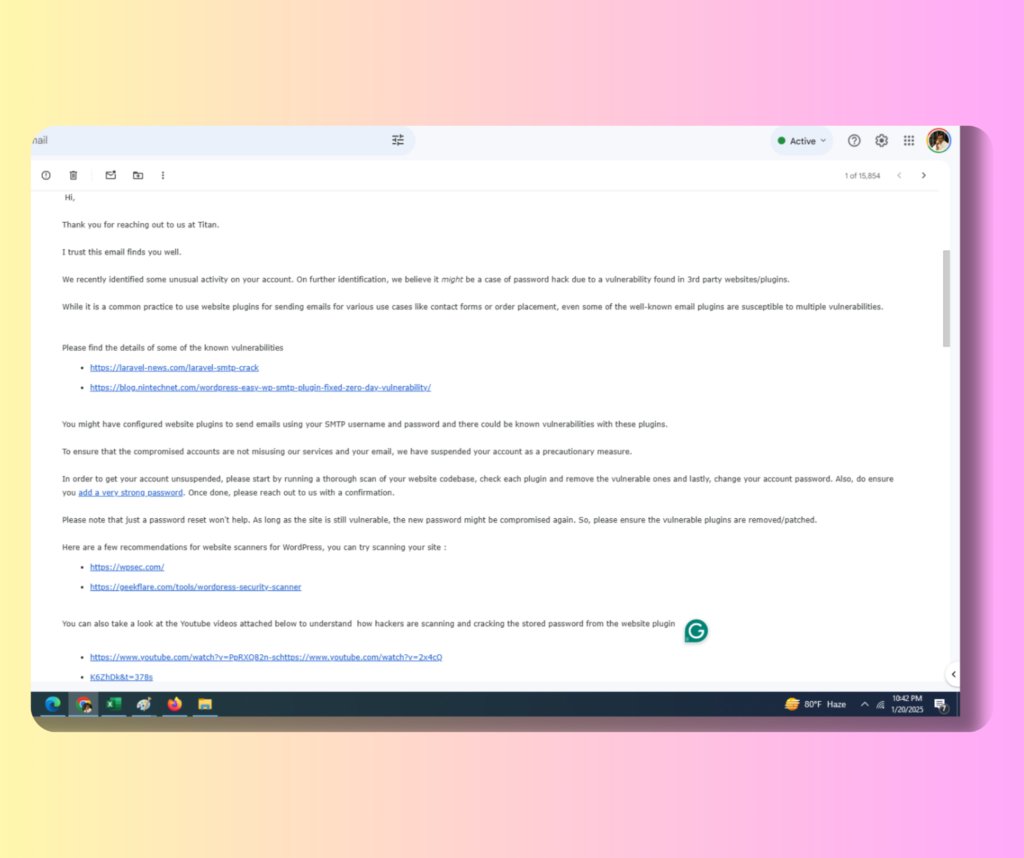
Soon after, I received a detailed response from Titan. Their email contained some technical insights, including information about vulnerabilities in my email account and website. Below is a screenshot of their response.
To summarize, Titan informed me that my account showed suspicious activity, potentially due to insecure plugins or weak configurations in my website’s backend. As a precautionary measure, they had suspended my email account to prevent further damage.
Reading this email was both shocking and eye-opening. On one hand, I felt like the sky had fallen on me—how could this happen? On the other hand, I was grateful to Titan for taking quick action to protect my account before the issue escalated further.
Steps I Took to Solve the Problem
The email from Titan contained a lot of technical terms and instructions that felt overwhelming at the time. I wasn’t sure where to start. So, I turned to ChatGPT for guidance.
This email was sent to you by Titan and contains important information regarding the security of your website account. The email outlines that some unusual activity has been detected on your account, which could be a case of password hacking caused by vulnerabilities in third-party websites or plugins.
Here are the key points explained:
1. Plugin Vulnerabilities:
Your website plugins (e.g., SMTP plugins) may have certain security weaknesses that hackers can exploit to access your account password.
- For example, vulnerabilities in Laravel or WordPress plugins can allow hackers to breach security.
2. Account Suspension:
Due to the detection of such unusual activities, Titan has temporarily suspended your account as a precautionary measure.
3. Encryption and Password Change:
You are advised to:
- Scan your website’s code and plugins for vulnerabilities.
- Remove or update any vulnerable plugins.
- Change your account password.
Note: Simply resetting your password will not be sufficient. If the plugins remain vulnerable, even a new password could be compromised again.
4. Website Scanning Tools:
To enhance your website’s security, Titan has suggested some tools for scanning and identifying vulnerabilities:
5. YouTube Videos:
To understand how hackers exploit plugin vulnerabilities to steal passwords, Titan has shared some YouTube links. These videos demonstrate the hacking methods and guide on how to secure your website.
6. DKIM Configuration:
Ensure that your domain is configured with DKIM (DomainKeys Identified Mail) records, if not already done. DKIM helps verify that your emails are not forged and improves email security.
7. Next Steps:
Titan has provided two specific scenarios and solutions:
- Case 1: If the SMTP plugin is not being used for critical business purposes, disable it.
- Case 2: If the plugin is essential for business operations, fix its vulnerabilities before resetting your password.
8. Additional Steps:
Titan has requested the following information to help identify the issue more effectively:
- The name of the plugin you are using (where SMTP details are configured).
- The Content Management System (CMS) your website uses (e.g., WordPress).
Important Note:
Titan cannot directly access your website or apply fixes. You must scan, patch, and secure your site yourself.
Final Remarks:
Titan has apologized for the inconvenience and thanked you for your cooperation in securing your account.
Still, it was the same technical terms. I couldn’t figure out what to do, so I asked GPT:
‘Now tell me step by step what I need to do according to this.‘
What GPT provided me, I have shared below exactly as it is for you all.
Step-by-Step Actions to Follow Based on Titan’s Email:
- Scan Your Website Code and Plugins:
- Perform a full scan of your website’s code and installed plugins, especially those using SMTP.
- Identify any plugins with vulnerabilities and either remove or update them.
- Use website scanning tools like:
- Fix Plugin Vulnerabilities:
- If any plugin vulnerabilities are detected, update or patch the affected plugins.
- In case the vulnerabilities are not publicly known, share the plugin names with Titan for further assistance.
- Change Your Password:
- Update your email account password with a strong and unique one.
- Use a combination of uppercase letters, lowercase letters, numbers, and special characters.
- Configure DKIM Records:
- Set up DKIM (DomainKeys Identified Mail) records for your domain to enhance email security.
- Proper DKIM configuration ensures better email authentication and prevents spam.
- Disable SMTP Plugin (If Necessary):
- Case 1: If you don’t use the SMTP plugin for critical business purposes, disable it.
- Case 2: If the SMTP plugin is essential for business operations, fix its vulnerabilities first and then reset your password before reactivating it.
- Inform Titan About Your Actions:
- If you have identified vulnerable plugins, share the names with Titan.
- Let them know which Content Management System (CMS) you are using (e.g., WordPress, Laravel, etc.).
- Confirm Completion of Steps:
- After completing the above steps, inform Titan that you have fixed the vulnerabilities, changed the password, and taken necessary actions. Request them to reactivate your account.
- Strengthen Security Further:
- Use security plugins like Wordfence or Sucuri to protect your website.
- Regularly monitor your website for security issues and apply updates promptly.
By following these steps, you can improve your website’s security and request Titan to lift the suspension on your account.
Now, I started working step by step according to the instructions:
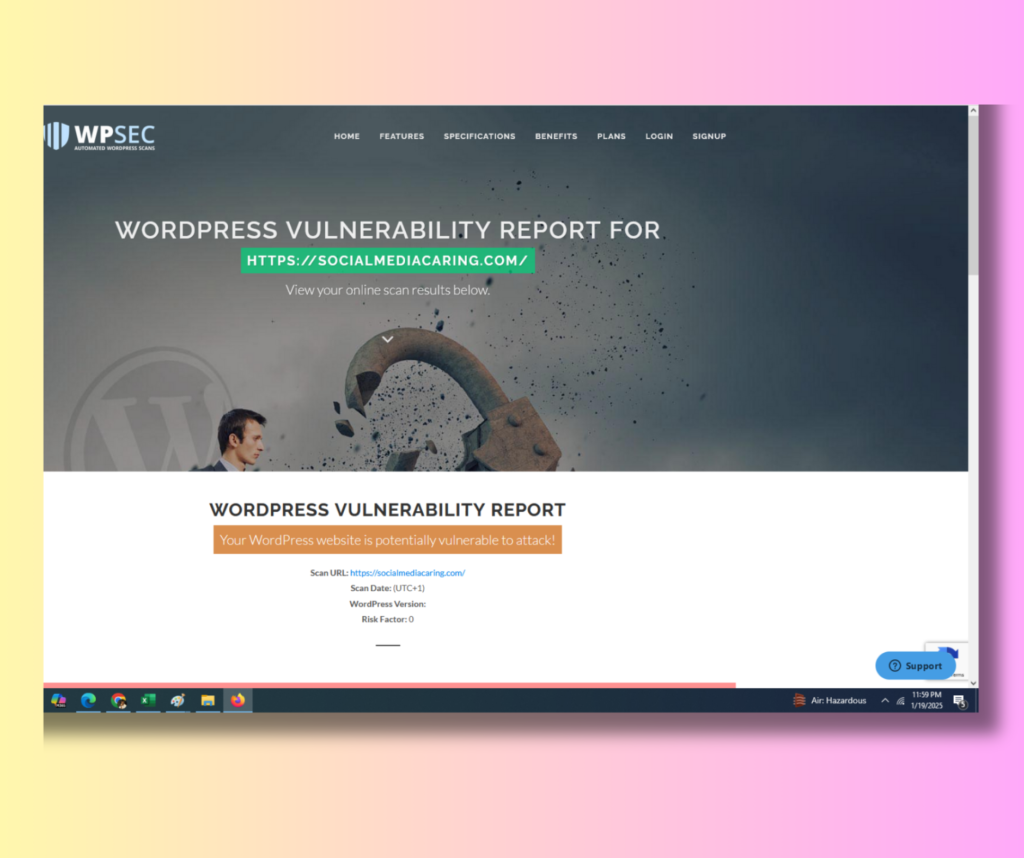
1. Scanning the Website
I went to the tools mentioned in Titan’s email to scan my website. At first, it said that it couldn’t find anything under my domain name. After carefully checking, I realized I had made a typing error—I had missed an “i” while typing the domain name. It was clear that I was feeling restless and anxious. Then I copied and pasted the domain name directly, but even after that, no vulnerable plugins or other security risks were detected. This gave me some relief, as it seemed my website was secure.
2. Removing Vulnerable Plugins
Since no vulnerabilities were found during the scan, there was no need to remove any plugins. This step was unnecessary in my case.
3. Securing the Password
I have always been very determined about password security. As a practice, I don’t log in to my email directly but instead access it through my hosting panel. Because of this setup, there wasn’t much to do regarding my email password. This step was also taken care of.
4. Attempting DKIM Configuration
DKIM is an email authentication method that ensures email security. However, I couldn’t locate or configure DKIM in my hosting panel. So, I reached out to my email provider for assistance. Although this was a pending issue, I documented everything and informed GPT about all the updates to ensure I wasn’t missing anything.
Subject: Request to Reactivate My Email Account
Dear Concern,
Thank you for your earlier email regarding the security concern. I appreciate your guidance and would like to update you on the actions I have taken so far to address the issue.
- I have thoroughly scanned my website’s codebase and reviewed all the plugins. After identifying potentially vulnerable plugins, I have deleted or replaced them with secure alternatives.
- I have ensured that my WordPress CMS and all installed plugins are up to date.
- I am currently using a strong password for my hosting account, which is secured with Google Authenticator. Since my email account is accessed directly through my Hostinger hosting panel, I believe the password is secure.
- Regarding DKIM: Unfortunately, I was unable to locate or configure the DKIM record. Could you kindly assist me with the steps required to set this up or verify it?
Additionally, I noticed that the YouTube links you shared in your email are inactive and not accessible. Please let me know if there are any alternative resources available.
For your reference, my website’s CMS is WordPress, and I am not using any SMTP plugins for sending emails.
I have followed all the necessary precautions you outlined and request you to kindly review my account status. Please let me know if there are any additional steps I need to take.
Thank you for your cooperation and support.
Best regards,
[Your Full Name][Your Email Address][Your Contact Number]
After that, they requested screenshots as proof of the security steps I had taken. I provided them with the necessary screenshots.
But this time, their reply was terrifying.
They sent me a link related to my site and informed me that this link was publicly exposing my email password. When I checked the link, I saw that it was indeed doing so.
This realization left me even more frightened
Hello,
I hope you are doing well.
Your ENV file is exposed along with your passwords.
You can check here – https://samplewebsite.com/.env
Please secure the above page as soon as possible and reset your password.
Once you take the two steps, we can unsuspend your email account
We look forward to hearing from you!
Regards,
At this point, I had no idea how to solve this issue. And how could I? These are deep technical matters, which I, as a regular person, am not supposed to know.
To figure things out, I turned to YouTube and searched for solutions. What I found, I’m now sharing with you:
First, I logged into the hosting file management system and searched for .ENV. I found it just as expected. Then, I right-clicked on the file and selected “Permissions.”
Under the “Other” option, I unchecked the box to ensure that no unauthorized person could access the file.
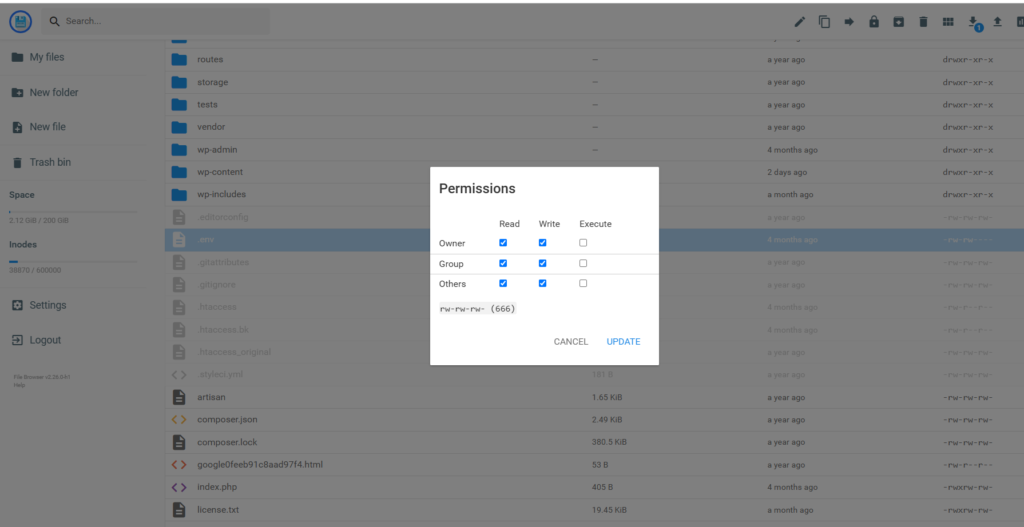
Next, it was time to inform Titan about the steps I had taken, hoping they would reactivate my business email.
Wow! They reactivated my email!
Tips to Protect Your Website from Hacking
- Use Security Plugins
Install security plugins like Wordfence or Sucuri to keep your website monitored and protected at all times. - Limit Login Attempts
Prevent brute-force attacks by limiting the number of login attempts on your website. - Take Regular Backups
Always maintain updated backups of your website to ensure recovery in case of any mishap. - Avoid Vulnerable Plugins
Research thoroughly before installing any plugin. Avoid plugins with known vulnerabilities or poor reviews. - Secure Email Configuration
Ensure proper configuration of email security protocols such as DKIM, SPF, and DMARC to safeguard against unauthorized access.
Conclusion
Every day, millions of websites are operated around the world. However, the complex and technical aspects that go on behind the scenes of a website are often overlooked—mainly because most users (and I’d say about 90%) are not aware of them. But I firmly believe it’s essential to pay attention to these aspects, as hackers or attackers exploit vulnerabilities with full knowledge and intent.
If managing these technicalities feels overwhelming, I recommend entrusting your website’s security to reliable service providers like Titan for email services and hosting giants like Hostinger or Namecheap. They’ve proven to be highly responsive in such situations.
Oh, and let’s not forget the incredible help ChatGPT can provide! It truly feels like a close friend in times of trouble, as you’ve probably realized through my experience.
Lastly, a heartfelt thanks to Titan for identifying and helping me fix the unknown vulnerabilities on my website. They’ve earned my trust for their proactive support.
- Backup Your Website
- Cybersecurity for Websites
- DKIM and SPF Setup
- Fix Website Vulnerabilities
- Hostinger
- Prevent Website Hacking
- Protect Your Website
- Safe Hosting Practices
- Secure Email Configuration
- Secure Plugins
- Secure WordPress
- Titan
- Vulnerable Websites
- Website Monitoring Tools
- Website Security
- WordPress Security Tips